Abstract
- Stingrays trick iPhones and Android gadgets alike into sharing delicate info, notably your IMSI quantity, which can be utilized for identification and monitoring.
- Android has non-obligatory protections like disabling 2G and blocking unencrypted communications, however help is determined by the precise telephone you might have, and which model of Android it is operating.
- iPhones have fewer defenses towards stingrays until you allow Lockdown Mode.
It has been over a decade for the reason that begin of the Snowden leaks, which uncovered mass surveillance packages within the US. I point out this as a result of one of many smaller issues Snowden (and others) drew consideration to is the usage of “stingrays,” also called IMSI catchers. Police, army, and intelligence companies have often used these to intercept knowledge on cellphone customers with out their data — and criminals could now be making use of the expertise as properly.
All this makes it sensible to be taught somewhat bit about how stingrays work, and how one can defend your iPhone or Android machine towards them, since nobody has an inherent proper to intercept your cellphone site visitors with no warrant. What’s attention-grabbing is that in the intervening time, Android 16 appears to supply a bonus on this space — although Apple will presumably catch up in the end.
Associated
Do you really need to worry about spyware on your phone?
It is a matter of the place you reside, what you do, and what your safety habits are like.
What’s a stingray, and the way does it work?
Preying on hidden vulnerabilities
Unsplash
The very first thing to level out is that legally talking, the time period “stingray” derives from a selected product — the StingRay, made by the Harris Company. It is so much simpler to speak about stingrays than IMSI catchers, nevertheless, so the product grew to become a catch-all time period, a lot as some individuals discuss with all facial tissues as Kleenex.
Functionally, stingrays trick your telephone into connecting to them by pretending to be a close-by mobile tower. As soon as that occurs, it is potential to extract delicate knowledge, together with your telephone’s IMSI (Worldwide Cell Subscriber Id) quantity, which can be utilized to establish and monitor you. Stingrays may additionally be used to gather metadata, and in some instances, the precise content material of communications. Extra hardly ever, stingrays are used as offensive weapons, say to conduct denial of service (DoS) assaults.
Any mobile machine inside vary of a stingray is susceptible to connecting to it, so your knowledge could also be snatched up even if you aren’t an supposed goal.
This may occasionally all sound like one thing your telephone ought to be capable to defend towards, however stingrays can dupe your telephone into utilizing a protocol with weaker safety, for example by briefly switching you from 5G to 2G, which most carriers have deserted. Usually, computerized hopping is an efficient factor — it retains you linked as you progress between areas with completely different protection. But when it is not dealt with correctly, it will probably develop into an assault vector.
One of many terrifying issues about stingrays is that they are non-discriminatory. That’s, any mobile machine inside vary of a stingray is susceptible to connecting to it, so your knowledge could also be snatched up even if you aren’t an supposed goal. This and different points have drawn the eye of scrutiny of teams just like the American Civil Liberties Union and the Digital Frontier Basis. There’s extra to clarify than I can probably go into right here, so I encourage you to be taught extra, notably in the event you’re planning to hitch a politically delicate protest.
Methods to defend an Android machine towards stingrays
The very best safety is reserved for the most recent gadgets
Crucial factor is retaining Android up-to-date, and being conscious of its anti-stingray choices. Should you’ve bought Android 12 or later, you may disable 2G connectivity utterly by going to Settings -> Community & Web -> SIMs, selecting your SIM, then toggling off Enable 2G. Don’t fret — most telephone carriers have switched solely to 4G and 5G, so you will not discover any calls, texts, or knowledge interrupted. Certainly even 3G networks are being deprecated, since they’re too sluggish to maintain up with the calls for of contemporary apps.
Android 14 expands this safety with an choice to dam “null ciphers,” i.e. unencrypted communications. There is not any official motive to be utilizing unencrypted knowledge anymore, given how harmful the web might be, so disabling null ciphers is an apparent means of mitigating the specter of stingray assaults. Android 15 takes yet one more step ahead, enabling a notification at any time when a community asks for distinctive machine identifiers, or forces weaker safety.
The one zero-risk choice, although, is to dam mobile exercise solely.
Android 16 features a Cell community safety web page to centralize issues, which you need to be capable to attain through Settings -> Safety & privateness -> Security Heart. There is a massive catch, nevertheless — it solely seems on gadgets with specific modems, and model 3.0 or later of Android’s IRadio {hardware} abstraction layer (HAL). You are unlikely to see the web page in any respect, even in the event you personal one thing as current as a Pixel 9. You might have to attend in your subsequent telephone improve to check this out.
The excellent news right here is that many Android telephones ought to help disabling 2G, at the least. It is simply much less handy and safe than what the most recent and best Android 16 gadgets are able to.
Should you’re in a high-risk scenario, there are apps that may doubtlessly warn you about stingrays, corresponding to SnoopSnitch. The one zero-risk choice, although, is to dam mobile exercise solely, and that applies to each iPhones and Android gadgets.

Associated
Is it safe to use Apple AirTags?
The dangers are normally very low, however you want to pay attention to them.
Methods to defend an iPhone towards stingrays
Time to play catch-up
Apple
iPhones are lagging behind on the subject of stingray safety, however they don’t seem to be defenseless. You’ll be able to, for instance, go to Settings -> Mobile -> Mobile Information Choices -> Voice & Information and select both 5G On or LTE. The 5G Auto choice does enhance battery life, however will increase your probabilities of being kicked right down to a much less safe community.
Should you use that step, you might also wish to go to Settings -> Mobile -> Community Choice and disable Computerized, however be warned — this feature can create havoc. You might end up unable to roam home networks, and you will have to manually choose a service if you journey overseas. It is in all probability not definitely worth the trouble.
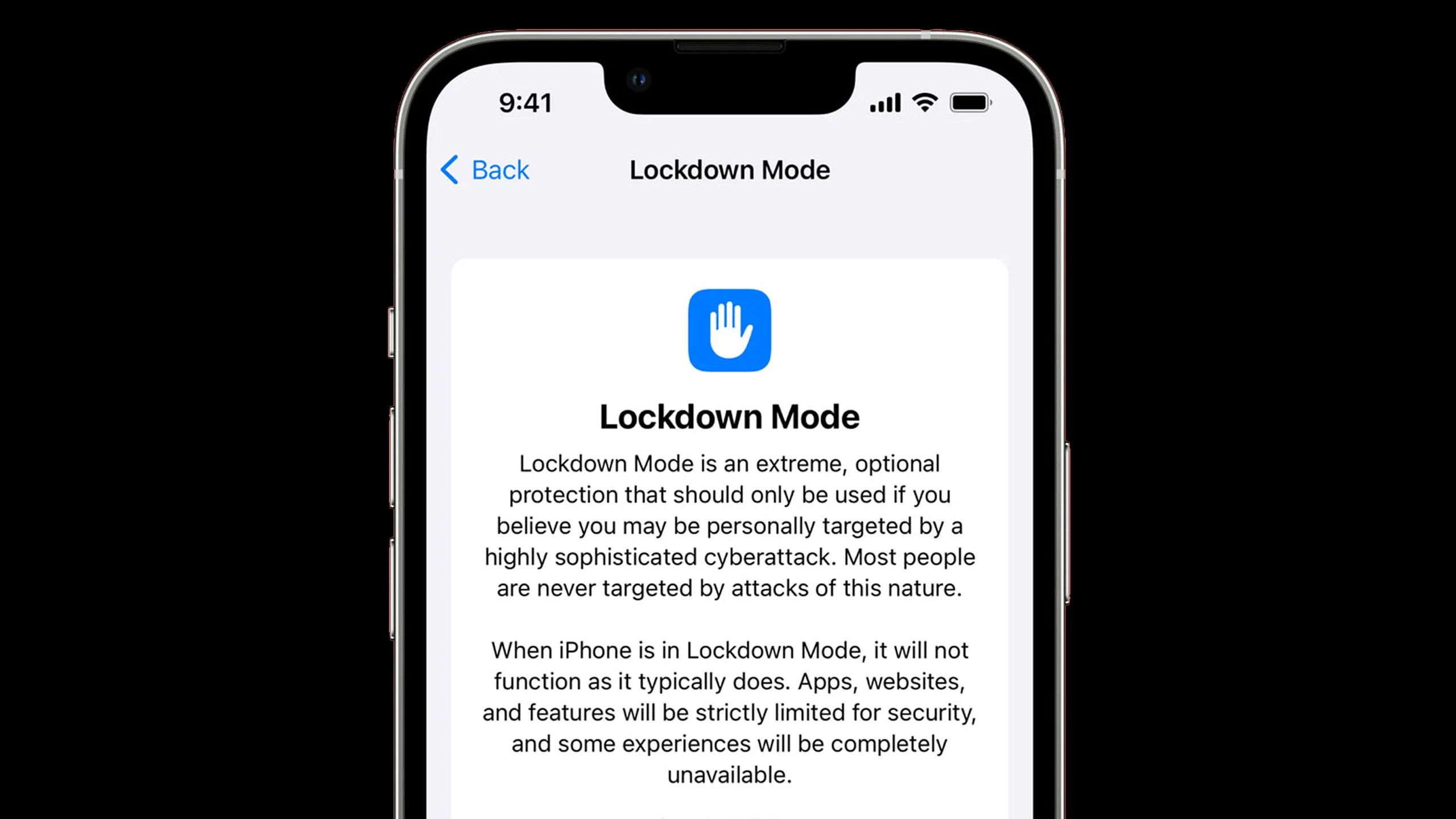
That is partly as a result of in iOS 16 or later, Apple presents a characteristic known as Lockdown Mode. This permits a large set of safety measures, largely supposed for journalists, dissidents, and others susceptible to being focused by authoritarian regimes or international governments. Should you’re really frightened about stingrays, although, Lockdown Mode forcibly disables 2G, and limits how your iPhone can work together with the skin world. It is so draconian that you need to keep away from it until completely obligatory — even many web sites and Messages attachments will not work.
It is not clear but whether or not iOS 26, coming fall 2025, will provide any enhancements to stingray safety. I am anticipating Apple to meet up with Android in some unspecified time in the future, nevertheless, for the reason that firm prides itself on safety and privateness.

You may additionally like
Everything you need to know about PEVs, or personal electric vehicles
You need to use PEVs like e-bikes and scooters to discover, run errands, or velocity up your commute.
Trending Merchandise

TP-Hyperlink AX5400 WiFi 6 Router (Archer AX73)- Twin Band Gigabit Wi-fi Web Router, Excessive-Pace ax Router for Streaming, Lengthy Vary Protection, 5 GHz

Amazon Fundamentals – 27 Inch IPS Monitor 75 Hz Powered with AOC Expertise FHD 1080P HDMI, Show Port and VGA Enter VESA Appropriate Constructed-in Audio system for Workplace and Residence, Black

acer Aspire 5 15 Slim Laptop computer | 15.6″ FHD (1920 x 1080) IPS |Core i7-1355U | Intel Iris Xe Graphics | 16GB LPDDR5 | 512GB Gen 4 SSD | Wi-Fi 6E | USB4/Thunderbolt 4 | Backlit KB | A515-58M-7570, Grey

NETGEAR 4-Stream WiFi 6 Router (R6700AX) â Security Features, AX1800 Wireless Speed (Up to 1.8 Gbps), Covers up to 1,500 sq. ft., 20 devices

Thermaltake Tower 500 Vertical Mid-Tower Pc Chassis Helps E-ATX CA-1X1-00M1WN-00

Logitech MK270 Wi-fi Keyboard And Mouse Combo For Home windows, 2.4 GHz Wi-fi, Compact Mouse, 8 Multimedia And Shortcut Keys, For PC, Laptop computer – Black

NETGEAR Nighthawk Professional Gaming WiFi 6 Router (XR1000) 6-Stream AX5400 Wi-fi Velocity (as much as 5.4Gbps) | DumaOS 3.0 Optimizes Lag-Free Server Connections 4 x 1G Ethernet and 1 USB Ports

SAMSUNG 27-Inch S43GC Series Business Essential Computer Monitor, IPS Panel, Height Adjustable Stand, Triple Input, New DisplayPort, 100Hz, AMD FreeSync, Advanced Eye Care LS27C432GANXZA, 2024